내부망용 시스템에 인증서를 생성하고 nginx를 통해 SSL 접속하는 방법을 정리한다.
작성일 : 2022-06-13 OS : Ubuntu 22.04 LTS
1> 서버용 키 생성
openssl genrsa -des3 -out private.key 2048
# 비밀번호를 입력하여 생성
-------------------------------------------------
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-------------------------------------------------
2> Root CA 인증서 생성
openssl req -x509 -new -nodes -key private.key -sha256 -days 365 -out rootCA.pem
# 1>에서 입력한 비밀번호 입력
-------------------------------------------------
Enter pass phrase for private.key:
# 인증서 정보 입력
-------------------------------------------------
Country Name (2 letter code) [AU]:KO
State or Province Name (full name) [Some-State]:SEOUL
Locality Name (eg, city) []:KangNam
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Opendocs
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:opd.kr
-------------------------------------------------
3> crt 파일로 변환
openssl x509 -outform der -in rootCA.pem -out rootCA.crt
4> 접속할 시스템에 인증서 등록
4-1> 윈도우
> 서버로 부터 rootCA.crt파일 다운로드
> 파일 더블클릭
> 인증서 설치(I)
> 로컬 컴퓨터(L)
> 모든 인증서를 다음 저장소에 저장(P)
> 찾아보기(R) > 신뢰할 수 있는 루트 인증 기관 선택 > 확인
> 다음(N) > 마침(F)
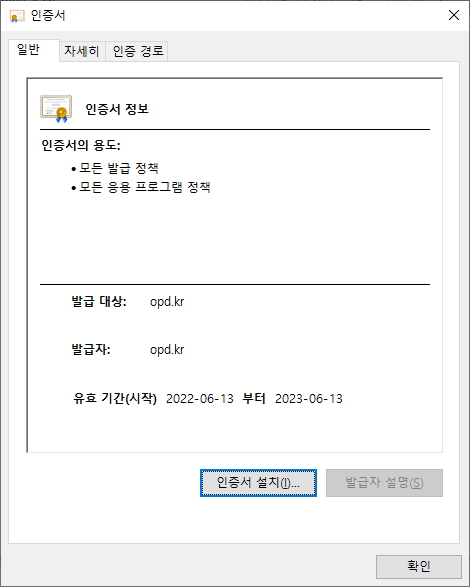
4-2> 맥
> 서버로 부터 rootCA.pem파일 다운로드
sudo security add-trusted-cert -d -r trustRoot -k "/Library/Keychains/System.keychain" rootCA.pem
5> Nginx 설치
# Install the prerequisites
apt install curl gnupg2 ca-certificates lsb-release ubuntu-keyring
# Fetch the key
curl https://nginx.org/keys/nginx_signing.key | gpg --dearmor \
| sudo tee /usr/share/keyrings/nginx-archive-keyring.gpg >/dev/null
# Verify Key
gpg --dry-run --quiet --import --import-options import-show /usr/share/keyrings/nginx-archive-keyring.gpg
# Set Up Stable Repo
echo "deb [signed-by=/usr/share/keyrings/nginx-archive-keyring.gpg] \
http://nginx.org/packages/ubuntu `lsb_release -cs` nginx" \
| sudo tee /etc/apt/sources.list.d/nginx.list
echo -e "Package: *\nPin: origin nginx.org\nPin: release o=nginx\nPin-Priority: 900\n" \
| sudo tee /etc/apt/preferences.d/99nginx
# Install nginx
sudo apt update
sudo apt install nginx=1.22.*
sudo systemctl start nginx
6> 사이트 인증서 생성
# 인증서 생성
openssl genrsa -out sample.opendocs.co.kr.key 2048
openssl req -new -key sample.opendocs.co.kr.key -out sample.opendocs.co.kr.csr
# ext 파일 생성
vi sample.opendocs.co.kr.ext
-------------------------------------------------
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = sample.opendocs.co.kr
-------------------------------------------------
# crt 파일 생성
openssl x509 -req -in sample.opendocs.co.kr.csr -CA rootCA.pem -CAkey private.key -CAcreateserial \
-out sample.opendocs.co.kr.crt -days 365 -sha256 -extfile sample.opendocs.co.kr.ext
# pem 파일 생성
openssl x509 -in sample.opendocs.co.kr.crt -outform PEM -out sample.opendocs.co.kr.pem
7> Nginx 사이트 설정
vi /etc/nginx/conf.d/sample.opendocs.co.kr.conf
server {
listen 443 ssl;
server_name sample.opendocs.co.kr;
ssl_certificate /etc/encrypt/sample.opendocs.co.kr.pem;
ssl_certificate_key /etc/encrypt/self/sample.opendocs.co.kr.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
proxy_pass https://172.20.0.104:8443;
}
}
8> Nginx 재시작
systemctl restart nginx
9> 사이트 접속시 자물쇠 확인
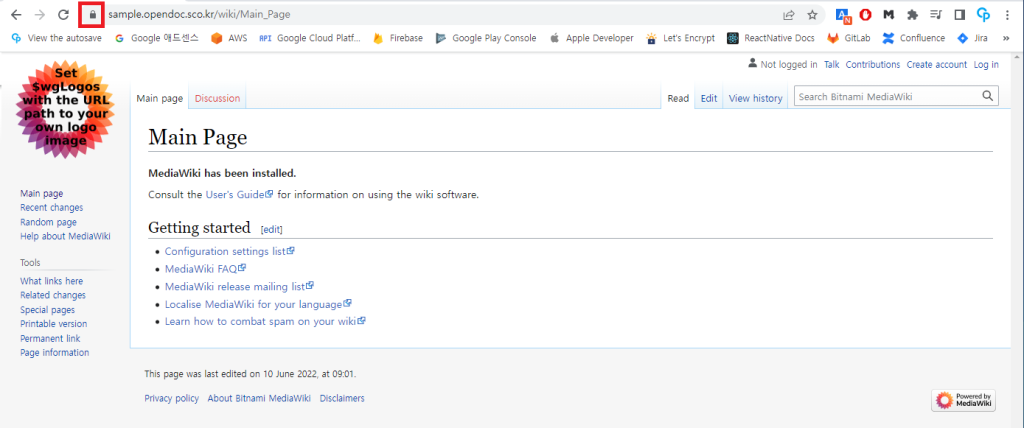
10> 사이트별 설정값
Docker 구성시 컨테이너 마다 프록시 설정값이 다름
( proxy_pass 부분이 상이함)
10-1> GitLab
server {
listen 443 ssl;
server_name gitlab.opendocs.co.kr;
ssl_certificate /etc/letsencrypt/self/gitlab.opendocs.co.kr.pem;
ssl_certificate_key /etc/letsencrypt/self/gitlab.opendocs.co.kr.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
proxy_pass http://127.0.0.1:9999;
}
}
10-2> Jenkins
server {
listen 443 ssl;
server_name jenkins.opendocs.co.kr;
ssl_certificate /etc/letsencrypt/self/jenkins.opendocs.co.kr.pem;
ssl_certificate_key /etc/letsencrypt/self/jenkins.opendocs.co.kr.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
proxy_pass http://127.0.0.1:8888;
}
}
10-3> SonarQube
server {
listen 443 ssl;
server_name sonar.opendocs.co.kr;
ssl_certificate /etc/letsencrypt/self/sonar.opendocs.co.kr.pem;
ssl_certificate_key /etc/letsencrypt/self/sonar.opendocs.co.kr.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
proxy_pass http://127.0.0.1:7777;
}
}
10-4> Wiki
server {
listen 443 ssl;
server_name wiki.opendocs.co.kr;
ssl_certificate /etc/letsencrypt/self/wiki.opendocs.co.kr.pem;
ssl_certificate_key /etc/letsencrypt/self/wiki.opendocs.co.kr.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
proxy_pass https://172.20.0.104:8443;
}
}
10-5> Redmine
server {
listen 443 ssl;
server_name issue.opendocs.co.kr;
ssl_certificate /etc/letsencrypt/self/issue.opendocs.co.kr.pem;
ssl_certificate_key /etc/letsencrypt/self/issue.opendocs.co.kr.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
proxy_pass http://127.0.0.1:5555;
}
}